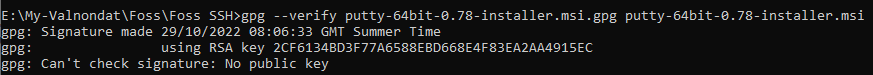
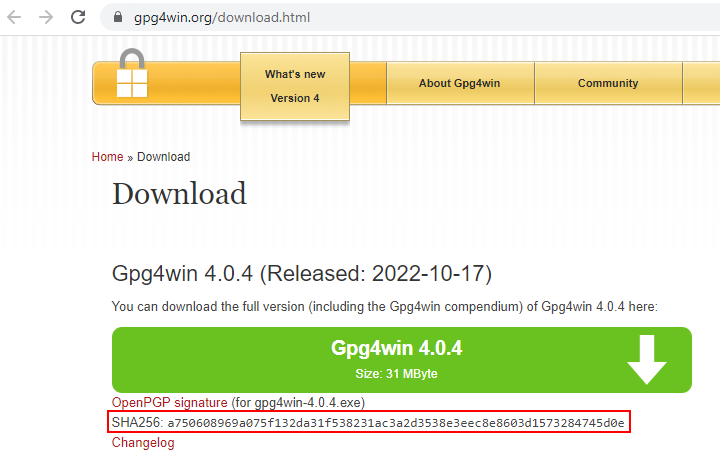
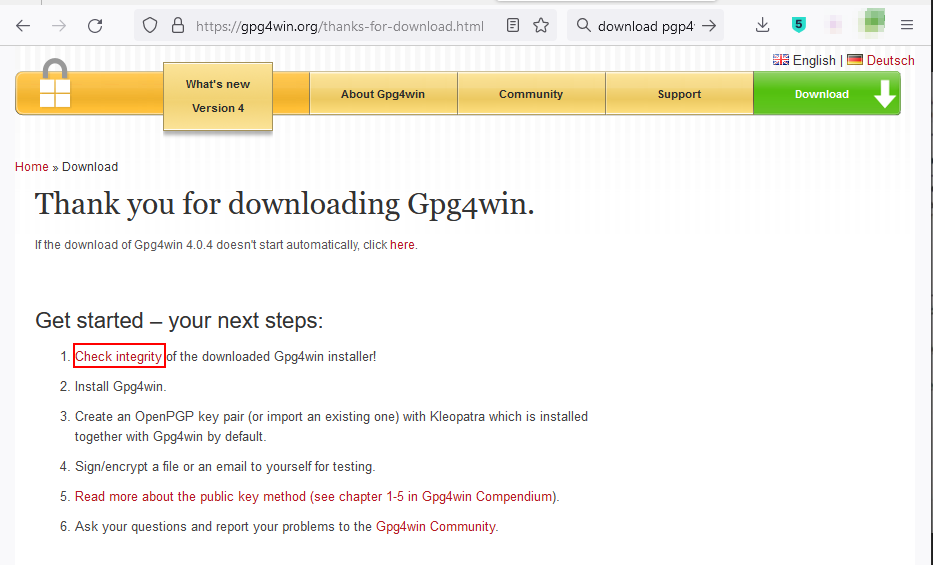
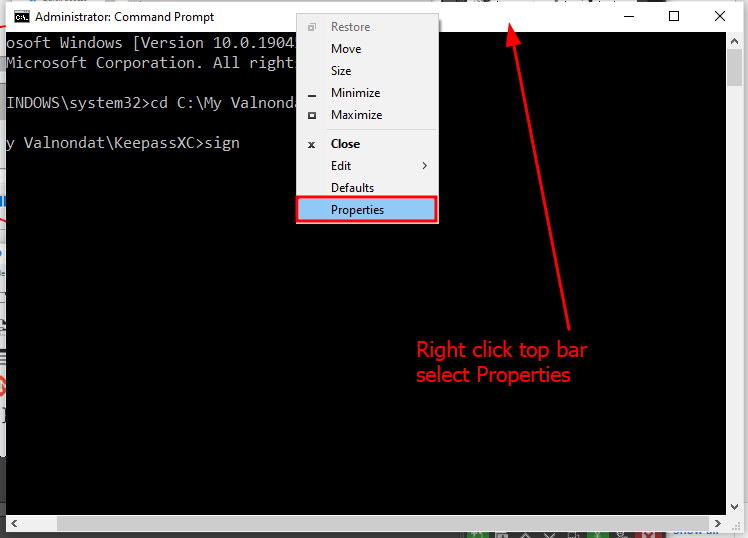
Several universities in the UK offer excellent programs in 3D animation. Here are some of the top ones:
- Bournemouth University: Known for its National Centre for Computer Animation (NCCA), Bournemouth University offers highly regarded courses in animation and visual effects.
- University of Hertfordshire: Their School of Creative Arts is well-known for its animation and 3D modeling programs.
- University of the Arts London (UAL): UAL offers various courses related to animation, including 3D animation, at institutions such as Central Saint Martins and London College of Communication.
- Teesside University: Their Animation and Visual Effects program is highly respected, offering opportunities to work on real-world projects.
- University of Westminster: Known for its strong emphasis on both theoretical knowledge and practical skills in animation and visual effects.
- Glasgow School of Art: Offers courses in animation and 3D modeling within its School of Simulation and Visualisation.
- University of Dundee: Their Animation program combines traditional animation techniques with digital technologies.
These universities provide a range of courses at undergraduate and postgraduate levels, with opportunities for specialization in various aspects of 3D animation, including character animation, visual effects, and storytelling. It’s also important to consider factors like faculty expertise, facilities, industry connections, and alumni success when choosing a university program.